Did Epstein’s Email Password Really Get Leaked?

© United States Marshals Service
After the U.S. Department of Justice’s release of millions of pages of documents tied to Jeffrey Epstein, some online commentators have claimed that passwords for Epstein’s personal email and other accounts were included in the files — and that tech-savvy users have “hacked” into his old email account using that information.
These posts have sparked conversation across social platforms and community threads, but the evidence behind the claims is currently unverified and incomplete.
What the Claims in the Emails Say
Several online posts — including threads on Reddit and news snippets shared on social platforms — assert that passwords for Epstein’s personal email accounts (such as Outlook, Yahoo and Apple ID logins) appeared in the newly released files and that people successfully accessed those accounts using the credentials. One widely shared claim lists alleged passwords such as ‘#1Island’, ‘ghislaine’ and ‘jenjen12’, attributed to messages in the released materials.
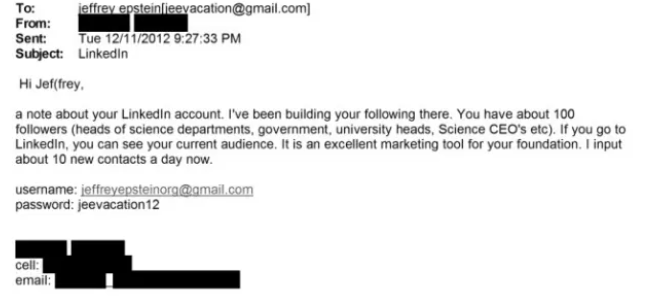
Some users have posted screenshots or comments implying they are “in Epstein’s Outlook” or that they’ve browsed messages, treating it like a direct login. Moreover, others discuss clustering around Reddit threads claiming to see login info referenced in the documents.
However, these accounts are community posts, not independently verified reporting from credible outlets confirming that anyone has actually accessed an active email account using leaked passwords.
Why the Epstein Password Reveal Is Unclear
There are a few important reasons to treat the online assertions cautiously:
1. No verified reporting from established news outlets:
At the time of writing, mainstream news organisations have not confirmed that Epstein’s email passwords were published in the DOJ file release or that anyone has legitimately logged into his accounts.
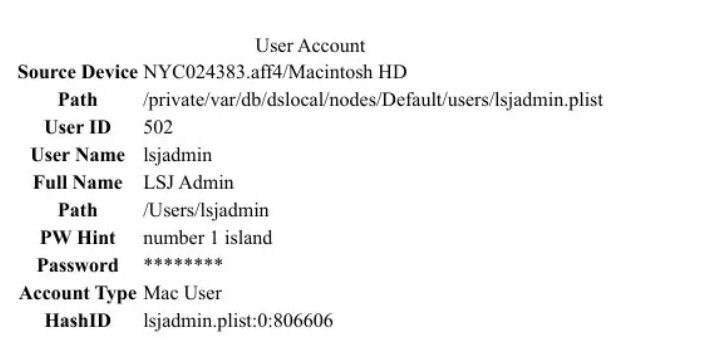
2. The “Jmail” project confuses the picture:
There is a browser-based archive called Jmail that presents Epstein’s released emails in a Gmail-style interface. This is not an actual login into his private email account, but rather a public tool that lets people browse Epstein’s archived messages made public under the Epstein Files Transparency Act.
3. Raw documents can include historical text:
The released files contain a massive volume of emails, attachments and unredacted text from Epstein’s communications — including old email content where usernames and passwords might be mentioned as text, not as login credentials for direct use. This doesn’t automatically mean live accounts are accessible.
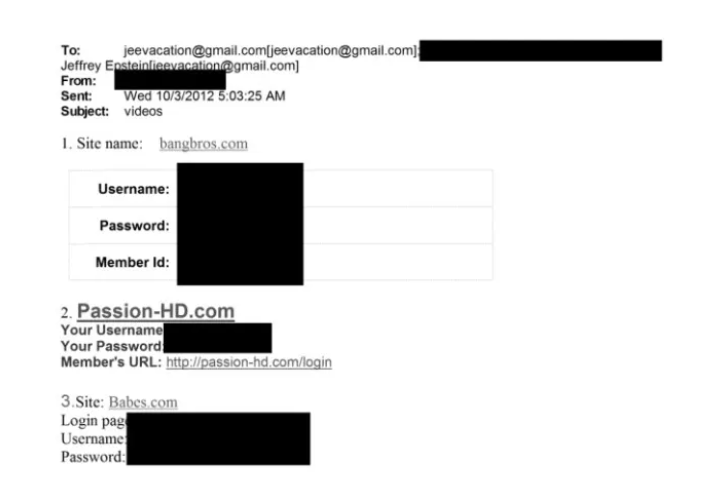
Security experts often warn that what looks like a password in a file can be an old reference, placeholder, or part of an unrelated document, and using such text as a login is generally ineffective without additional context (like matching the correct email server or account). There’s also no confirmation that these alleged passwords correspond to current, active accounts.
Broader Redaction and Security Issues in Epstein Files
Separately, the Department of Justice has acknowledged problems with the initial release of the Epstein files, including the accidental exposure of sensitive personal details of victims and others in some documents — which prompted removal and re-redaction of parts of the published material.
The large volume of material, heavy redactions and the availability of layered PDFs can make coded or embedded information appear where it wasn’t intended to be visible — but that doesn’t equate to confirmed security vulnerabilities or live account breaches. Analysts caution that raw data dumps can be misleading without proper context or technical verification.
You might also want to read: Epstein Files Email Suggests Jeffrey May Have Had a Secret Child


